Information Hiding Course
Welcome to the Information Hiding Course page! This course aims to explore the theoretical foundations and practical applications of information hiding technologies.
Innovation Practice
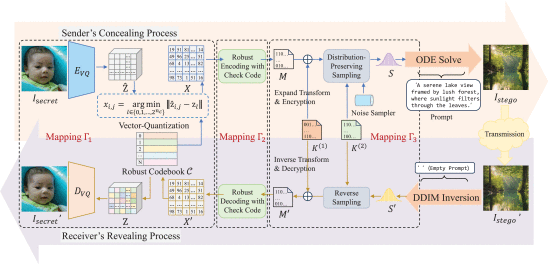
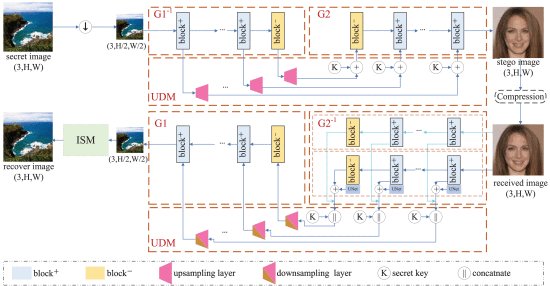
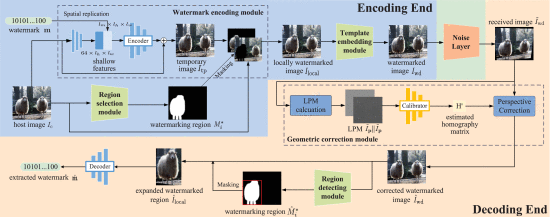
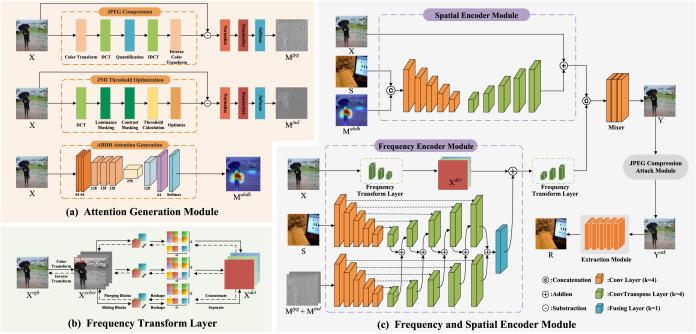
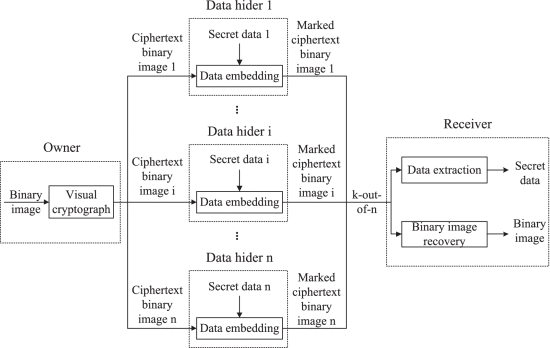
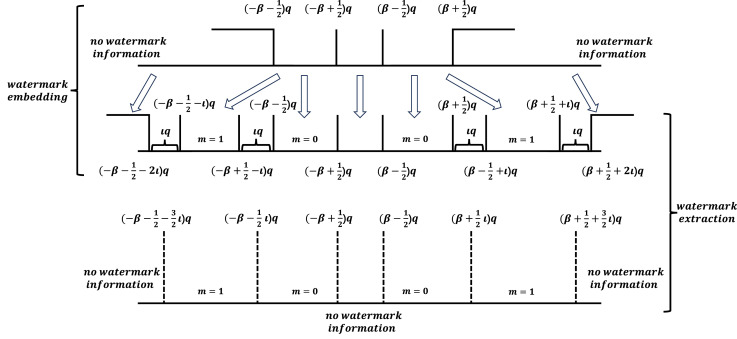
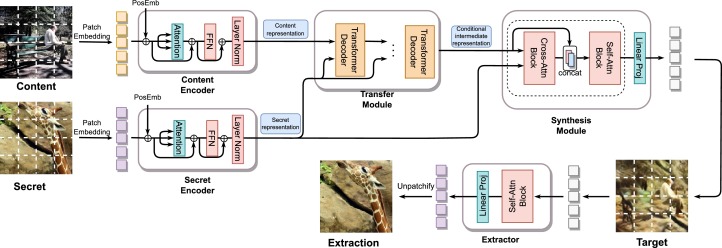
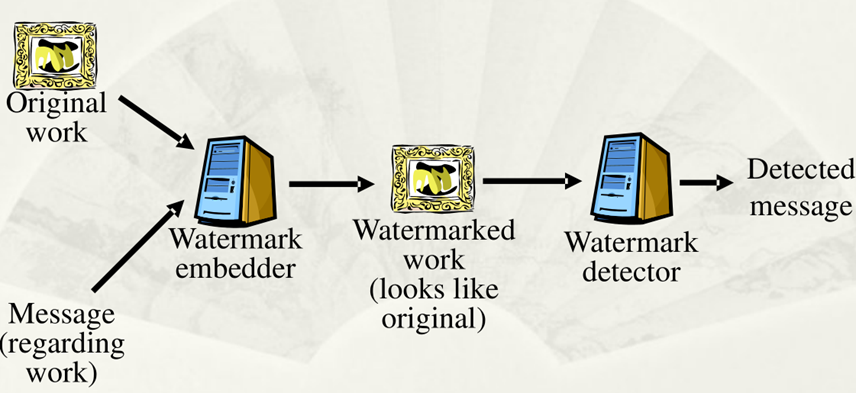
Innovation Practice Projects
Generative Steganography Research
Exploring generative information hiding techniques based on deep learning
Robust Hiding Algorithms
Developing compression-resistant and attack-resistant information hiding methods
Multimedia Watermarking Technology
Research on copyright protection for multimedia content such as images and videos
Covert Communication Systems
Building secure communication platforms based on information hiding
Course Materials
Course PPT
Detailed course slide materials covering theoretical foundations to practical applications


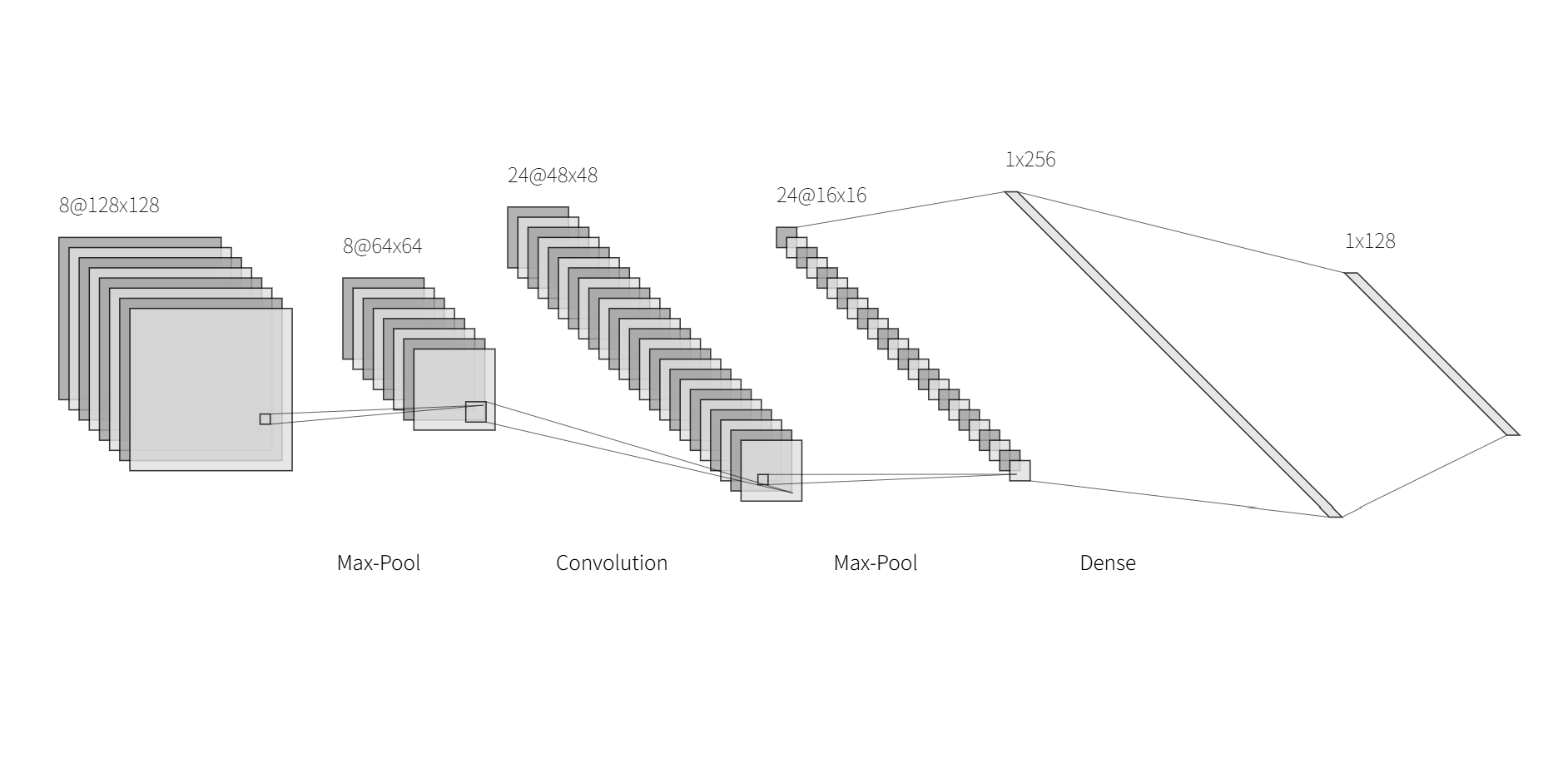
Practical Tools
Experimental Code Repository
Course experiment code examples and implementation templates
Access RepositoryEvaluation Tools
Performance evaluation and analysis tools for information hiding algorithms
Get ToolsExtended Reading
Professional WeChat Public Accounts
China Society of Image and Graphics (CSIG)
Steganography Alliance
Recommended Journals and Conferences
IEEE Transactions on Information Forensics and Security
Top-tier journal in information security
ACM Transactions on Multimedia Computing, Communications, and Applications
Multimedia technology journal
International Workshop on Digital Watermarking (IWDW)
International workshop on digital watermarking
Media Watermarking, Security, and Forensics
SPIE multimedia security conference
If you have any questions or need further learning resources, please feel free to contact us!